Microsoft announced that the Copilot Studio extension for the Visual Studio Code (VS Code) integrated development environment is now available to all users. […] Read More
Managing just-in-time access at scale is a growing IAM challenge as speed and auditability collide daily. Tines shows how automated workflows can grant, track, and revoke temporary app access without manual effort. […] Read More
The internet never stays quiet. Every week, new hacks, scams, and security problems show up somewhere. This week’s stories show how fast attackers change their tricks, how small mistakes turn into big risks, and how the same old tools keep finding new ways to break in. Read on to catch up before the next wave […]
The Gootloader malware, typically used for initial access, is now using a malformed ZIP archive designed to evade detection by concatenating up to 1,000 archives. […] Read More
Hackers are actively exploiting a maximum severity flaw in the Modular DS WordPress plugin that allows them to bypass authentication remotely and access the vulnerable sites with admin-level privileges. […] Read More
Food delivery platform Grubhub has confirmed a recent data breach after hackers accessed its systems, with sources telling BleepingComputer the company is now facing extortion demands. […] Read More
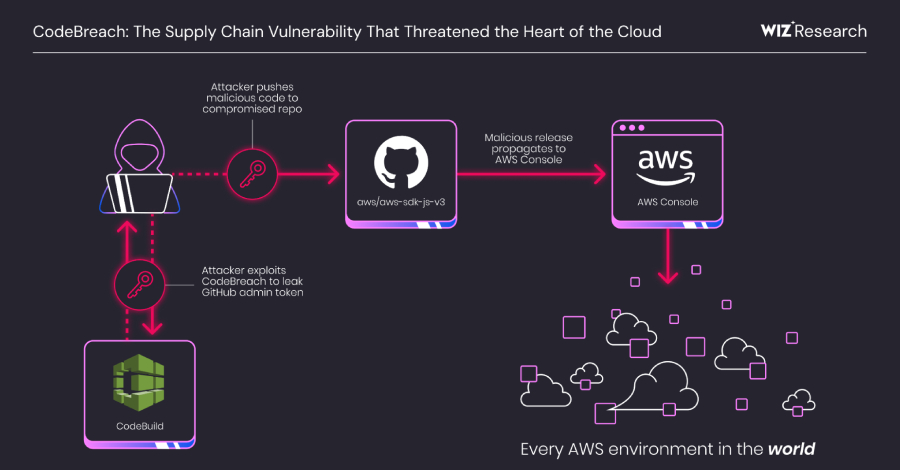
A critical misconfiguration in Amazon Web Services (AWS) CodeBuild could have allowed complete takeover of the cloud service provider’s own GitHub repositories, including its AWS JavaScript SDK, putting every AWS environment at risk. The vulnerability has been codenamed CodeBreach by cloud security company Wiz. The issue was fixed by AWS in September 2025 following responsible […]
Verizon has confirmed that yesterday’s nationwide wireless outage was caused by a software issue, though the company has not shared additional details about what went wrong. […] Read More
A critical vulnerability in Google’s Fast Pair protocol can allow attackers to hijack Bluetooth audio accessories like wireless headphones and earbuds, track users, and eavesdrop on their conversations. […] Read More
The upcoming Winter Games in the Italian Alps are attracting both hacktivists looking to reach billions of people and state-sponsored cyber-spies targeting the attending glitterati. Read More