A new family of Android click-fraud trojans leverages TensorFlow machine learning models to automatically detect and interact with specific advertisement elements. […] Read More
How bunq handles 97% of support with Amazon BedrockArtificial Intelligence In this post, we show how bunq upgraded Finn, its in-house generative AI assistant, using Amazon Bedrock to transform user support and banking operations to be seamless, in multiple languages and time zones.
In this post, we show how bunq upgraded Finn, its in-house generative AI assistant, using Amazon Bedrock to transform user support and banking operations to be seamless, in multiple languages and time zones. Read More
Using Strands Agents to create a multi-agent solution with Meta’s Llama 4 and Amazon BedrockArtificial Intelligence In this post, we explore how to build a multi-agent video processing workflow using Strands Agents, Meta’s Llama 4 models, and Amazon Bedrock to automatically analyze and understand video content through specialized AI agents working in coordination. To showcase the solution, we will use Amazon SageMaker AI to walk you through the code.
In this post, we explore how to build a multi-agent video processing workflow using Strands Agents, Meta’s Llama 4 models, and Amazon Bedrock to automatically analyze and understand video content through specialized AI agents working in coordination. To showcase the solution, we will use Amazon SageMaker AI to walk you through the code. Read More
7 Statistical Concepts Every Data Scientist Should Master (and Why)KDnuggets Understanding data starts with statistics. These 7 statistics concepts give you the foundation to analyze and interpret with confidence.
Understanding data starts with statistics. These 7 statistics concepts give you the foundation to analyze and interpret with confidence. Read More
Navigating AI Entrepreneurship: Insights From The Application LayerKDnuggets Through the lens of a serial entrepreneur, this article explores how the AI revolution is shifting from infrastructure to the application layer, where the greatest opportunities lie in solving specialized, data-heavy industry problems rather than perfecting raw technology.
Through the lens of a serial entrepreneur, this article explores how the AI revolution is shifting from infrastructure to the application layer, where the greatest opportunities lie in solving specialized, data-heavy industry problems rather than perfecting raw technology. Read More
Threat actors are exploiting misconfigured web applications used for security training and internal penetration testing, such as DVWA, OWASP Juice Shop, Hackazon, and bWAPP, to gain access to cloud environments of Fortune 500 companies and security vendors. […] Read More
Zoom and GitLab have released security updates to resolve a number of security vulnerabilities that could result in denial-of-service (DoS) and remote code execution. The most severe of the lot is a critical security flaw impacting Zoom Node Multimedia Routers (MMRs) that could permit a meeting participant to conduct remote code execution attacks. The vulnerability, […]
Microsoft shared a temporary workaround for customers experiencing Outlook freezes after installing this month’s Windows security updates. […] Read More
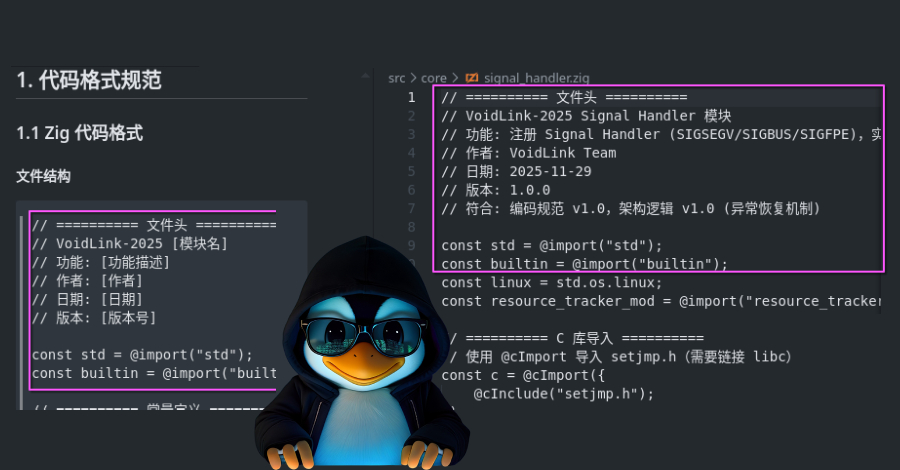
The recently discovered sophisticated Linux malware framework known as VoidLink is assessed to have been developed by a single person with assistance from an artificial intelligence (AI) model. That’s according to new findings from Check Point Research, which identified operational security blunders by malware’s author that provided clues to its developmental origins. The latest insight […]
LastPass is alerting users to a new active phishing campaign that’s impersonating the password management service, which aims to trick users into giving up their master passwords. The campaign, which began on or around January 19, 2026, involves sending phishing emails claiming upcoming maintenance and urging them to create a local backup of their password […]