Classification: PublicReporting Period: January 19-26, 2026Distribution: Security Operations, IT Leadership, Executive TeamPrepared By: Tech Jacks Solutions Security Intelligence TJS Weekly Security Intelligence Briefing – Week of Jan 26th 20261. Executive Summary The week of January 19-26, 2026 presents an elevated risk posture driven by four actively exploited vulnerabilities requiring immediate action: Cisco Unified Communications zero-day […]
Classification: PublicReporting Period: January 12-19, 2026Distribution: Security Operations, IT Leadership, Executive TeamPrepared By: Tech Jacks Solutions Security Intelligence TJS Weekly Security Intelligence Briefing – Week of Jan 19th 2026 Executive Summary The week of January 12-19, 2026 presents an elevated risk posture driven by Microsoft’s January Patch Tuesday release addressing 114 vulnerabilities (including one actively […]
Multiple current and former Target employees confirmed that leaked source code samples posted by a threat actor match real internal systems. The company also rolled out an “accelerated” lockdown of its Git server, requiring VPN access, a day after being contacted by BleepingComputer. […] Read More
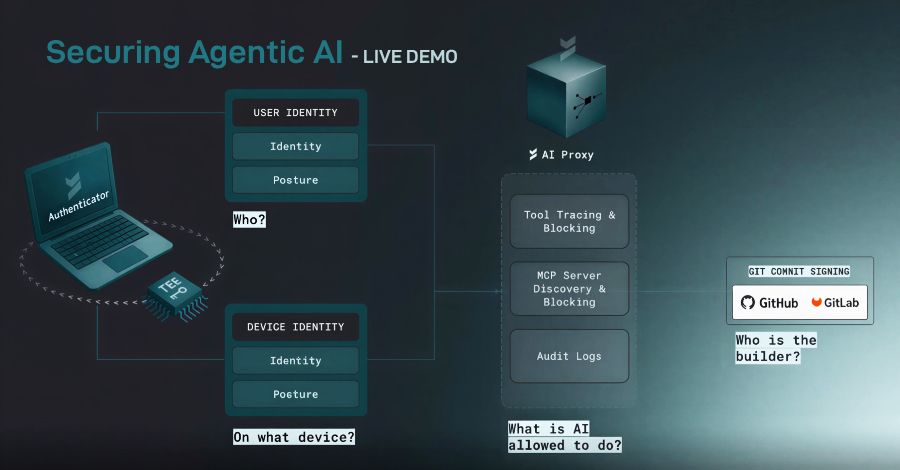
AI agents are no longer just writing code. They are executing it. Tools like Copilot, Claude Code, and Codex can now build, test, and deploy software end-to-end in minutes. That speed is reshaping engineering—but it’s also creating a security gap most teams don’t see until something breaks. Behind every agentic workflow sits a layer few […]
Scammers are flooding LinkedIn posts with fake “reply” comments that appear to come from the platform, warning of bogus policy violations and urging users to click external links. Some even abuse LinkedIn’s official lnkd.in shortener, making the phishing attempts harder to spot. […] Read More
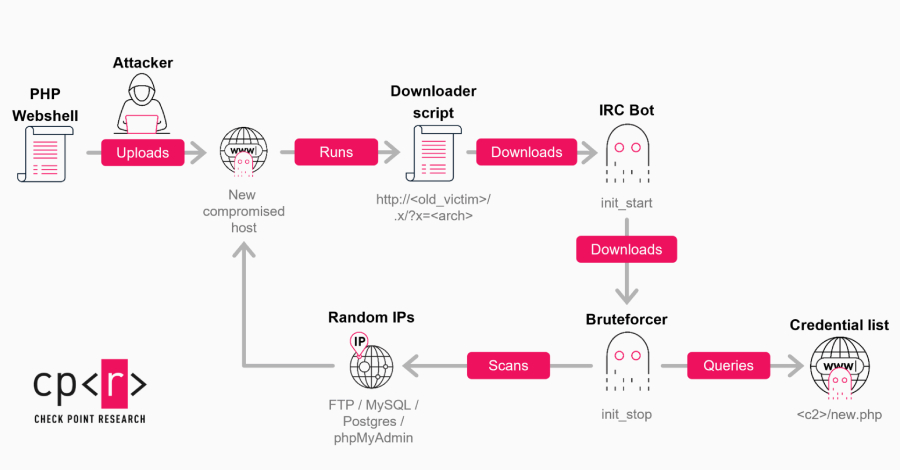
A new wave of GoBruteforcer attacks has targeted databases of cryptocurrency and blockchain projects to co-opt them into a botnet that’s capable of brute-forcing user passwords for services such as FTP, MySQL, PostgreSQL, and phpMyAdmin on Linux servers. “The current wave of campaigns is driven by two factors: the mass reuse of AI-generated server deployment […]
This week made one thing clear: small oversights can spiral fast. Tools meant to save time and reduce friction turned into easy entry points once basic safeguards were ignored. Attackers didn’t need novel tricks. They used what was already exposed and moved in without resistance. Scale amplified the damage. A single weak configuration rippled out […]
Nearly 60,000 n8n instances exposed online remain unpatched against a maximum-severity vulnerability dubbed “Ni8mare.” […] Read More
Microsoft 365 has made file sharing effortless, but that convenience often leaves organizations with little visibility into who can access sensitive data. Tenfold explains how access reviews for shared cloud content can help organizations regain visibility, reduce unnecessary permissions, and prevent data leaks in Microsoft 365. […] Read More
Here are the top cloud security trends I’m seeing in my crystal ball for the New Year — particularly arming us for AI adoption. Read More