A Spanish court has granted precautionary measures against NordVPN and ProtonVPN, ordering the two popular VPN providers to block 16 websites that facilitate piracy of football matches. […] Read More
Cybersecurity researchers have disclosed that artificial intelligence (AI) assistants that support web browsing or URL fetching capabilities can be turned into stealthy command-and-control (C2) relays, a technique that could allow attackers to blend into legitimate enterprise communications and evade detection. The attack method, which has been demonstrated against Microsoft Copilot and xAI Grok Read More
Keenadu downloads payloads that hijack browser searches, commit ad fraud, and execute other actions without user knowledge. Read More
A newly discovered and sophisticated Android malware called Keenadu has been found embedded in firmware from multiple device brands, enabling it to compromise all installed applications and gain unrestricted control over infected devices. […] Read More
ClickFix campaigns have adapted to the latest defenses with a new technique to trick users into infecting their own machines with malware. Read More
Singapore & Its 4 Major Telcos Fend Off Chinese Hackers darkreadingRobert Lemos, Contributing Writer
After detecting a zero-day attack, the country’s effective response was attributed to the tight relationship between its government and private industry. Read More
Classification: Public | Reporting Period: February 2–16, 2026 | Distribution: Security Operations, IT Leadership, Executive Team | Prepared By: Tech Jacks Solutions Security Intelligence TJS Weekly Security Intelligence Briefing – Week of Feb 16th ! Risk Posture CRITICAL Active Zero-Days 6+ CISA KEV Additions 3+ Reporting Period Feb 2–16, 2026 1. Executive Summary The period […]
Cloud attacks move fast — faster than most incident response teams. In data centers, investigations had time. Teams could collect disk images, review logs, and build timelines over days. In the cloud, infrastructure is short-lived. A compromised instance can disappear in minutes. Identities rotate. Logs expire. Evidence can vanish before analysis even begins. Cloud forensics […]
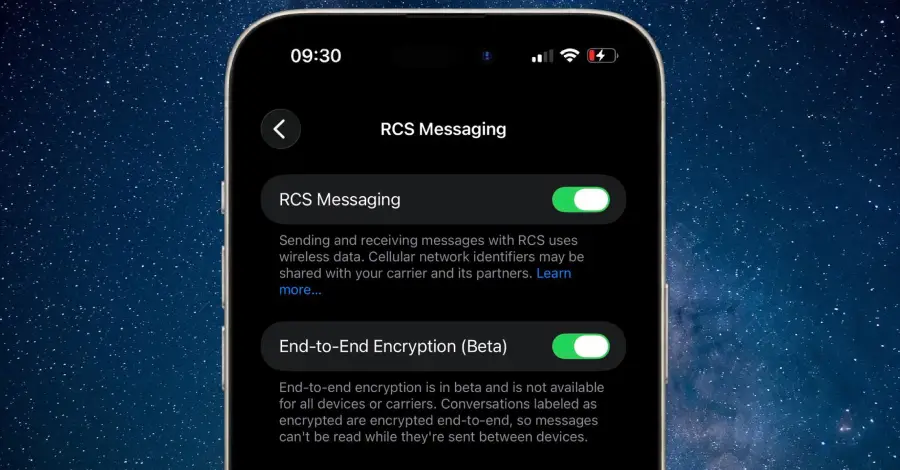
Apple on Monday released a new developer beta of iOS and iPadOS with support for end-to-end encryption (E2EE) in Rich Communications Services (RCS) messages. The feature is currently available for testing in iOS and iPadOS 26.4 Beta, and is expected to be shipped to customers in a future update for iOS, iPadOS, macOS, and watchOS. […]
Cybersecurity researchers have disclosed details of a new SmartLoader campaign that involves distributing a trojanized version of a Model Context Protocol (MCP) server associated with Oura Health to deliver an information stealer known as StealC. “The threat actors cloned a legitimate Oura MCP Server – a tool that connects AI assistants to Oura Ring health […]