Today, the United States, the United Kingdom, and Australia announced sanctions targeting Russian bulletproof hosting (BPH) providers that have supported ransomware gangs and other cybercrime operations. […] Read More
Google’s Gemini 3 is finally here, and we’re impressed with the results, but it still does not adhere to my requests as well as Claude Code. […] Read More
A critical flaw in the W3 Total Cache (W3TC) WordPress plugin can be exploited to run PHP commands on the server by posting a comment that contains a malicious payload. […] Read More
A second zero-day vulnerability in its web application firewall (WAF) line has come under attack, raising more questions about the vendor’s disclosure practices. Read More
A recently disclosed security flaw impacting 7-Zip has come under active exploitation in the wild, according to an advisory issued by the U.K. NHS England Digital on Tuesday. The vulnerability in question is CVE-2025-11001 (CVSS score: 7.0), which allows remote attackers to execute arbitrary code. It has been addressed in 7-Zip version 25.00 released in […]
Sneaky2FA, a popular among cybercriminals phishing-as-a-service (PhaaS) kit, has added Browser-in-the-Browser (BitB) capabilities, giving “customers” the option to launch highly deceptive attacks. […] Read More
When international corporations have to balance competing cyber laws from different countries, the result is fragmented, potentially vulnerable systems. Read More
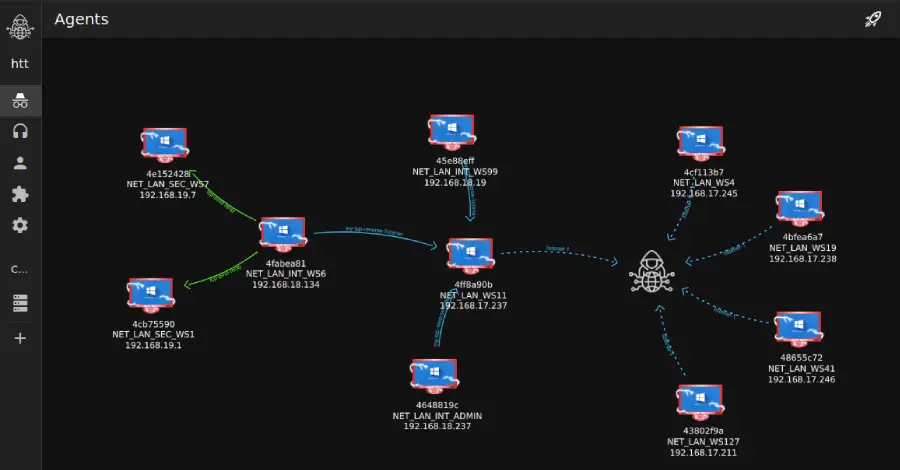
Cybersecurity researchers have disclosed details of a cyber attack targeting a major U.S.-based real-estate company that involved the use of a nascent command-and-control (C2) and red teaming framework known as Tuoni. “The campaign leveraged the emerging Tuoni C2 framework, a relatively new, command-and-control (C2) tool (with a free license) that delivers stealthy, in-memory payloads,” Read More
Suspected espionage-driven threat actors from Iran have been observed deploying backdoors like TWOSTROKE and DEEPROOT as part of continued attacks aimed at aerospace, aviation, and defense industries in the Middle East. The activity has been attributed by Google-owned Mandiant to a threat cluster tracked as UNC1549 (aka Nimbus Manticore or Subtle Snail), which was first […]
Identity security fabric (ISF) is a unified architectural framework that brings together disparate identity capabilities. Through ISF, identity governance and administration (IGA), access management (AM), privileged access management (PAM), and identity threat detection and response (ITDR) are all integrated into a single, cohesive control plane. Building on Gartner’s definition of “identity Read More