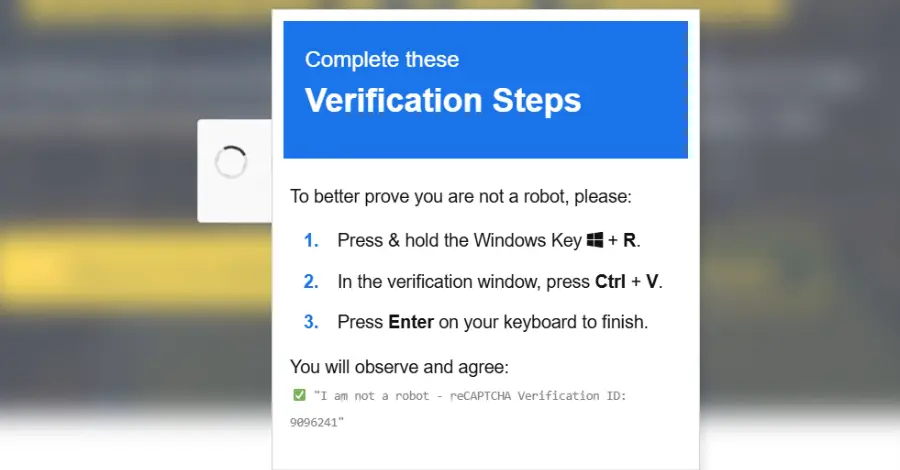
Cybersecurity researchers have disclosed details of a new campaign that combines ClickFix-style fake CAPTCHAs with a signed Microsoft Application Virtualization (App-V) script to distribute an information stealer called Amatera. “Instead of launching PowerShell directly, the attacker uses this script to control how execution begins and to avoid more common, easily recognized execution paths,” Read More
A critical-severity vulnerability in the vm2 Node.js sandbox library, tracked as CVE-2026-22709, allows escaping the sandbox and executing arbitrary code on the underlying host system. […] Read More
A Nebraska federal grand jury charged 31 additional defendants for their involvement in an ATM jackpotting operation allegedly orchestrated by members of the Venezuelan gang Tren de Aragua. […] Read More
The Chinese espionage threat group Mustang Panda has updated its CoolClient backdoor to a new variant that can steal login data from browsers and monitor the clipboard. […] Read More
The malware-as-a-service kit enables malicious extensions to overlay pages on real websites without changing the visible URL, signaling a fresh challenge for enterprise security. Read More
Fortinet has confirmed a new, actively exploited critical FortiCloud single sign-on (SSO) authentication bypass vulnerability, tracked as CVE-2026-24858, and says it has mitigated the zero-day attacks by blocking FortiCloud SSO connections from devices running vulnerable firmware versions. […] Read More
Data Science as Engineering: Foundations, Education, and Professional IdentityTowards Data Science Recognize data science as an engineering practice and structure education accordingly.
The post Data Science as Engineering: Foundations, Education, and Professional Identity appeared first on Towards Data Science.
Recognize data science as an engineering practice and structure education accordingly.
The post Data Science as Engineering: Foundations, Education, and Professional Identity appeared first on Towards Data Science. Read More
3 Ways to Anonymize and Protect User Data in Your ML PipelineKDnuggets In this article, you will learn three practical ways to protect user data in real-world ML pipelines, with techniques that data scientists can implement directly in their workflows.
In this article, you will learn three practical ways to protect user data in real-world ML pipelines, with techniques that data scientists can implement directly in their workflows. Read More
Build an intelligent contract management solution with Amazon Quick Suite and Bedrock AgentCoreArtificial Intelligence This blog post demonstrates how to build an intelligent contract management solution using Amazon Quick Suite as your primary contract management solution, augmented with Amazon Bedrock AgentCore for advanced multi-agent capabilities.
This blog post demonstrates how to build an intelligent contract management solution using Amazon Quick Suite as your primary contract management solution, augmented with Amazon Bedrock AgentCore for advanced multi-agent capabilities. Read More
The Multimodal AI Guide: Vision, Voice, Text, and BeyondKDnuggets AI systems now see images, hear speech, and process video, understanding information in its native form.
AI systems now see images, hear speech, and process video, understanding information in its native form. Read More