A self-spreading package published on npm spams the registry by spawning new packages every every seven seconds, creating large volumes of junk. […] Read More
The ImunifyAV malware scanner for Linux server, used by tens of millions of websites, is vulnerable to a remote code execution vulnerability that could be exploited to compromise the hosting environment. […] Read MoreThe ImunifyAV malware scanner for Linux server, used by tens of millions of websites, is vulnerable to a remote code execution vulnerability that could be […]
In 2025, employees are still using weak passwords. Instead of forcing an impossible change, security leaders are working around the problem. Read MoreIn 2025, employees are still using weak passwords. Instead of forcing an impossible change, security leaders are working around the problem.
The Washington Post is notifying nearly 10,000 employees and contractors that some of their personal and financial data has been exposed in the Oracle data theft attack. […] Read MoreThe Washington Post is notifying nearly 10,000 employees and contractors that some of their personal and financial data has been exposed in the Oracle data theft attack. […]
Kerberoasting attacks let hackers steal service account passwords and escalate to domain admin, often without triggering alerts. Specops Software shares how auditing AD passwords, enforcing long unique credentials, and using AES encryption can shut these attacks down early. […] Read MoreKerberoasting attacks let hackers steal service account passwords and escalate to domain admin, often without triggering […]
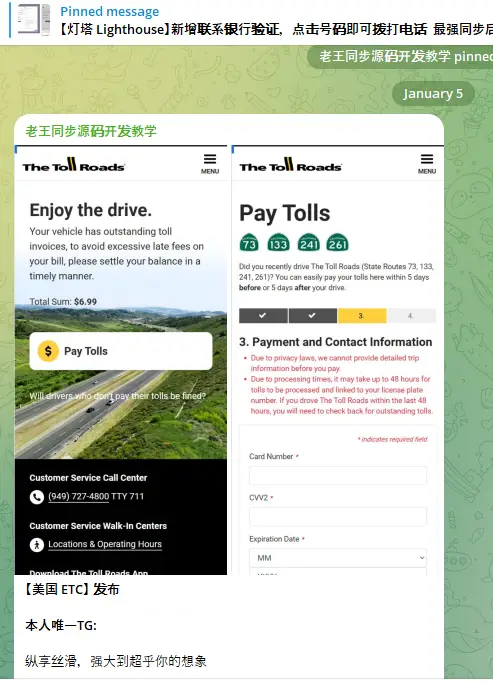
Google is suing more than two dozen unnamed individuals allegedly involved in peddling a popular China-based mobile phishing service that helps scammers impersonate hundreds of trusted brands, blast out text message lures, and convert phished payment card data into mobile wallets from Apple and Google. In a lawsuit filed in the Southern District of New […]
South America’s largest country is notorious for banking malware attacks; Maverick self-terminates if its targeted user is based outside Brazil. Read MoreSouth America’s largest country is notorious for banking malware attacks; Maverick self-terminates if its targeted user is based outside Brazil.
Microsoft is rolling out a new Teams feature for Premium customers that will automatically block screenshots and recordings during meetings. […] Read MoreMicrosoft is rolling out a new Teams feature for Premium customers that will automatically block screenshots and recordings during meetings. […]
Understanding neural networks through sparse circuitsOpenAI News OpenAI is exploring mechanistic interpretability to understand how neural networks reason. Our new sparse model approach could make AI systems more transparent and support safer, more reliable behavior.
OpenAI is exploring mechanistic interpretability to understand how neural networks reason. Our new sparse model approach could make AI systems more transparent and support safer, more reliable behavior. Read More
IBM: Data silos are holding back enterprise AIAI News According to IBM, the primary barrier holding back enterprise AI isn’t the technology itself but the persistent issue of data silos. Ed Lovely, VP and Chief Data Officer at IBM, describes data silos as the “Achilles’ heel” of modern data strategy. Lovely made the comments following the release of a new study from the IBM
The post IBM: Data silos are holding back enterprise AI appeared first on AI News.
According to IBM, the primary barrier holding back enterprise AI isn’t the technology itself but the persistent issue of data silos. Ed Lovely, VP and Chief Data Officer at IBM, describes data silos as the “Achilles’ heel” of modern data strategy. Lovely made the comments following the release of a new study from the IBM
The post IBM: Data silos are holding back enterprise AI appeared first on AI News. Read More