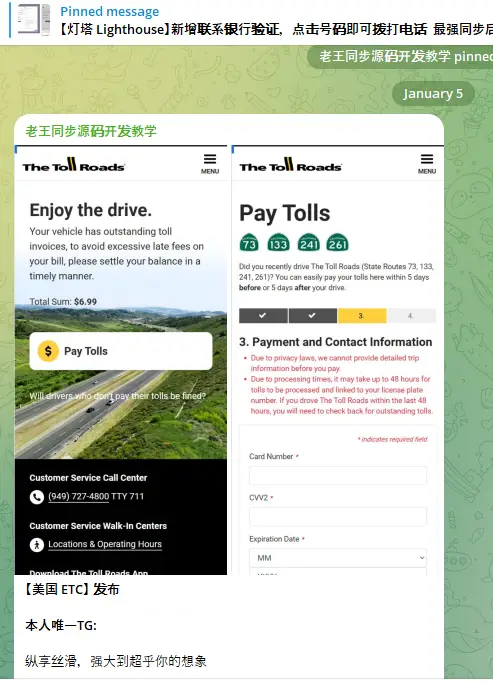
Google is suing more than two dozen unnamed individuals allegedly involved in peddling a popular China-based mobile phishing service that helps scammers impersonate hundreds of trusted brands, blast out text message lures, and convert phished payment card data into mobile wallets from Apple and Google. In a lawsuit filed in the Southern District of New […]
South America’s largest country is notorious for banking malware attacks; Maverick self-terminates if its targeted user is based outside Brazil. Read MoreSouth America’s largest country is notorious for banking malware attacks; Maverick self-terminates if its targeted user is based outside Brazil.
Microsoft is rolling out a new Teams feature for Premium customers that will automatically block screenshots and recordings during meetings. […] Read MoreMicrosoft is rolling out a new Teams feature for Premium customers that will automatically block screenshots and recordings during meetings. […]
LLMs Are Randomized AlgorithmsTowards Data Science A surprising connection between the newest AI models and a 50-year old academic field
The post LLMs Are Randomized Algorithms appeared first on Towards Data Science.
A surprising connection between the newest AI models and a 50-year old academic field
The post LLMs Are Randomized Algorithms appeared first on Towards Data Science. Read More
Robotics with Python: Q-Learning vs Actor-Critic vs Evolutionary AlgorithmsTowards Data Science Build a Custom 3D Environment for your RL Robot
The post Robotics with Python: Q-Learning vs Actor-Critic vs Evolutionary Algorithms appeared first on Towards Data Science.
Build a Custom 3D Environment for your RL Robot
The post Robotics with Python: Q-Learning vs Actor-Critic vs Evolutionary Algorithms appeared first on Towards Data Science. Read More
Processing Large Datasets with Dask and Scikit-learnKDnuggets This article uncovers how to harness Dask for scalable data processing, even under limited hardware constraints.This article uncovers how to harness Dask for scalable data processing, even under limited hardware constraints.
This article uncovers how to harness Dask for scalable data processing, even under limited hardware constraints.This article uncovers how to harness Dask for scalable data processing, even under limited hardware constraints. Read More
IBM: Data silos are holding back enterprise AIAI News According to IBM, the primary barrier holding back enterprise AI isn’t the technology itself but the persistent issue of data silos. Ed Lovely, VP and Chief Data Officer at IBM, describes data silos as the “Achilles’ heel” of modern data strategy. Lovely made the comments following the release of a new study from the IBM
The post IBM: Data silos are holding back enterprise AI appeared first on AI News.
According to IBM, the primary barrier holding back enterprise AI isn’t the technology itself but the persistent issue of data silos. Ed Lovely, VP and Chief Data Officer at IBM, describes data silos as the “Achilles’ heel” of modern data strategy. Lovely made the comments following the release of a new study from the IBM
The post IBM: Data silos are holding back enterprise AI appeared first on AI News. Read More
Understanding neural networks through sparse circuitsOpenAI News OpenAI is exploring mechanistic interpretability to understand how neural networks reason. Our new sparse model approach could make AI systems more transparent and support safer, more reliable behavior.
OpenAI is exploring mechanistic interpretability to understand how neural networks reason. Our new sparse model approach could make AI systems more transparent and support safer, more reliable behavior. Read More
A Russian-speaking threat behind an ongoing, mass phishing campaign has registered more than 4,300 domain names since the start of the year. The activity, per Netcraft security researcher Andrew Brandt, is designed to target customers of the hospitality industry, specifically hotel guests who may have travel reservations with spam emails. The campaign is said to […]
Cybersecurity researchers have uncovered a malicious Chrome extension that poses as a legitimate Ethereum wallet but harbors functionality to exfiltrate users’ seed phrases. The name of the extension is “Safery: Ethereum Wallet,” with the threat actor describing it as a “secure wallet for managing Ethereum cryptocurrency with flexible settings.” It was uploaded to the Chrome […]