The key elements in a security operations center’s strategy map very closely to the swim/bike/run events in a triathlon. SOCs, like triathletes, perform well when their “inputs” are strong. Read More
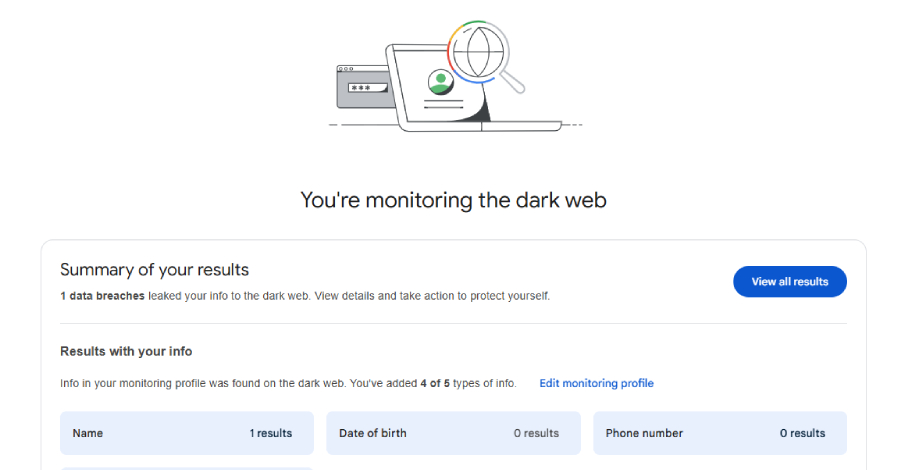
Google has announced that it’s discontinuing its dark web report tool in February 2026, less than two years after it was launched as a way for users to monitor if their personal information is found on the dark web. To that end, scans for new dark web breaches will be stopped on January 15, 2026, […]
A new malware-as-a-service (MaaS) information stealer named SantaStealer is being advertised on Telegram and hacker forums as operating in memory to avoid file-based detection. […] Read More
Two Apple zero-day vulnerabilities discovered this month have overlap with another mysterious zero-day flaw Google patched last week. Read More
Google is discontinuing its “dark web report” security tool, stating that it wants to focus on other tools it believes are more helpful. […] Read More
Japanese e-commerce giant Askul Corporation has confirmed that RansomHouse hackers stole around 740,000 customer records in the ransomware attack it suffered in October. […] Read More
700Credit, a U.S.-based financial services and fintech company, will start notifying more than 5.8 million people that their personal information has been exposed in a data breach incident. […] Read More
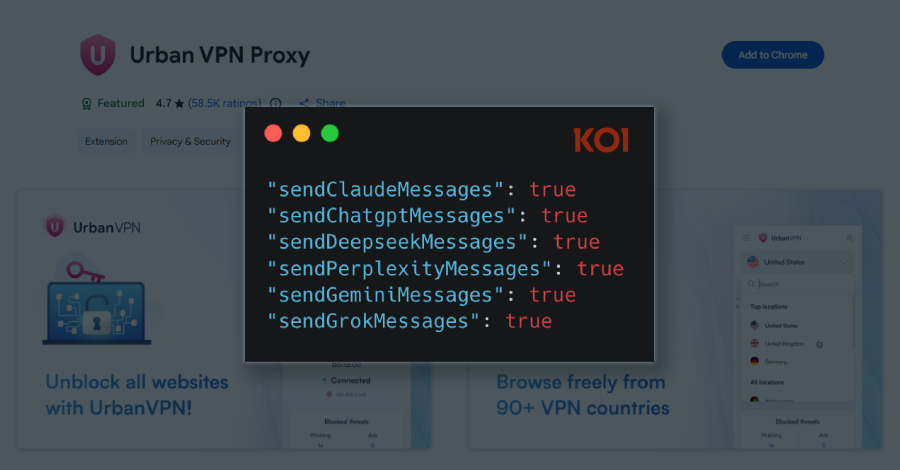
A Google Chrome extension with a “Featured” badge and six million users has been observed silently gathering every prompt entered by users into artificial intelligence (AI)-powered chatbots like OpenAI ChatGPT, Anthropic Claude, Microsoft Copilot, DeepSeek, Google Gemini, xAI Grok, Meta AI, and Perplexity. The extension in question is Urban VPN Proxy, which has a 4.7 […]
Users accessing the SoundCloud audio streaming platform through a virtual private network (VPN) connection are denied access to the service and see a 403 ‘forbidden’ error. […] Read More
Etay Mayor, a cybersecurity strategist and professor, shares his journey, insights, and advice on breaking into the diverse and ever-evolving field of cybersecurity. Read More