Researchers discovered a security weakness in the AI-powered coding tool that allows malicious MCP server to hijack Cursor’s internal browser. Read More
Microsoft is working to resolve a known issue preventing users from installing the Microsoft 365 desktop apps on Windows devices. […] Read More
Cybersecurity researchers have discovered malware campaigns using the now-prevalent ClickFix social engineering tactic to deploy Amatera Stealer and NetSupport RAT. The activity, observed this month, is being tracked by eSentire under the moniker EVALUSION. First spotted in June 2025, Amatera is assessed to be an evolution of ACR (short for “AcridRain”) Stealer, which was available […]
A Princeton University database was compromised in a cyberattack on November 10, exposing the personal information of alumni, donors, faculty members, and students. […] Read More
The police in the Netherlands have seized around 250 physical servers powering a bulletproof hosting service in the country used exclusively by cybercriminals for providing complete anonymity. […] Read More
Microsoft: Azure hit by 15 Tbps DDoS attack using 500,000 IP addresses BleepingComputerSergiu Gatlan
Microsoft said today that the Aisuru botnet hit its Azure network with a 15.72 terabits per second (Tbps) DDoS attack, launched from over 500,000 IP addresses. […] Read More
This week showed just how fast things can go wrong when no one’s watching. Some attacks were silent and sneaky. Others used tools we trust every day — like AI, VPNs, or app stores — to cause damage without setting off alarms. It’s not just about hacking anymore. Criminals are building systems to make money, […]
Phishing attacks are no longer confined to the email inbox, with 1 in 3 phishing attacks now taking place over non-email channels like social media, search engines, and messaging apps. LinkedIn in particular has become a hotbed for phishing attacks, and for good reason. Attackers are running sophisticated spear-phishing attacks against company executives, with recent […]
The threat actor known as Dragon Breath has been observed making use of a multi-stage loader codenamed RONINGLOADER to deliver a modified variant of a remote access trojan called Gh0st RAT. The campaign, which is primarily aimed at Chinese-speaking users, employs trojanized NSIS installers masquerading as legitimate like Google Chrome and Microsoft Teams, according to […]
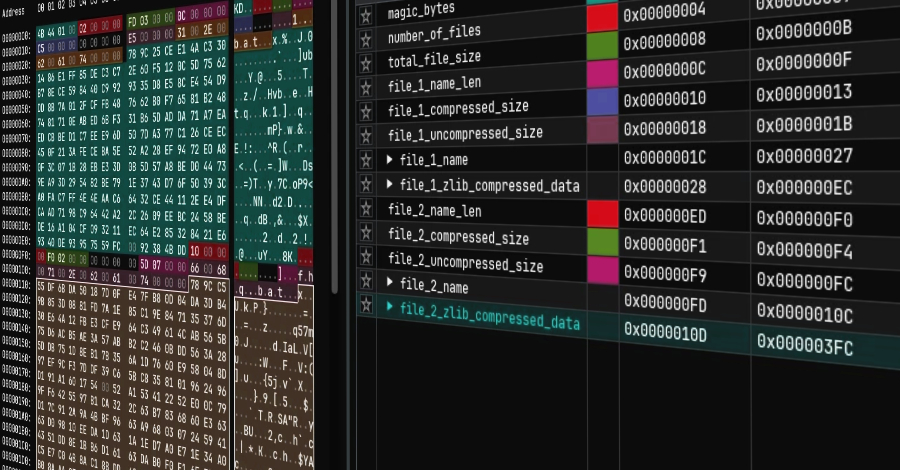
In diary entry “Formbook Delivered Through Multiple Scripts“, Xavier mentions that the following line: Nestlers= array(79+1,79,80+7,60+9,82,83,72,69,76,76) decodes to the string POWERSHELL. My tool numbers-to-hex.py is a tool that extracts numbers from text files, and converts them to hexadecimal. Like this: I can then use another tool, hex-to-bin.py to convert the hexadecimal numbers to binary, and […]