The actor behind the “Contagious Interview” campaign is continuing to refine its tactics and social engineering scams to wrest credentials from macOS users. Read More
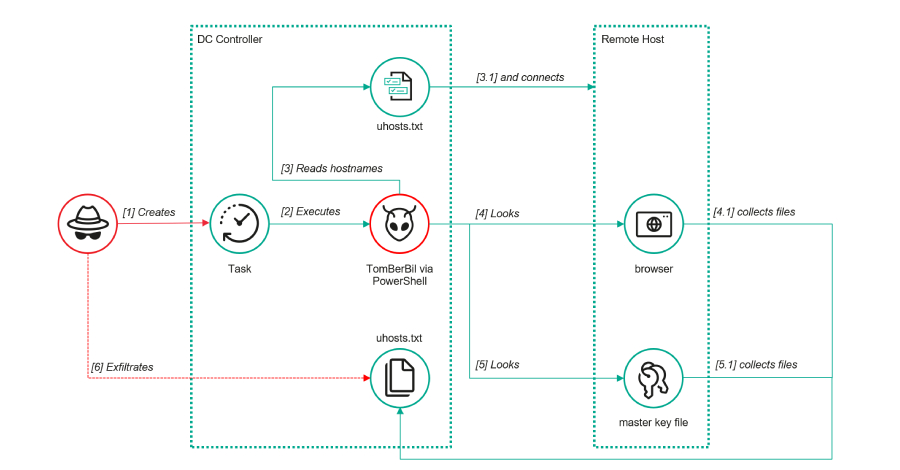
The threat actor known as ToddyCat has been observed adopting new methods to obtain access to corporate email data belonging to target companies, including using a custom tool dubbed TCSectorCopy. “This attack allows them to obtain tokens for the OAuth 2.0 authorization protocol using the user’s browser, which can be used outside the perimeter of […]
Microsoft says it will add a new Teams call handler beginning in January 2026 to reduce launch times and boost call performance for the Windows desktop client. […] Read More
New research reveals that sophisticated phishing attacks consistently bypass traditional enterprise security measures. Read More
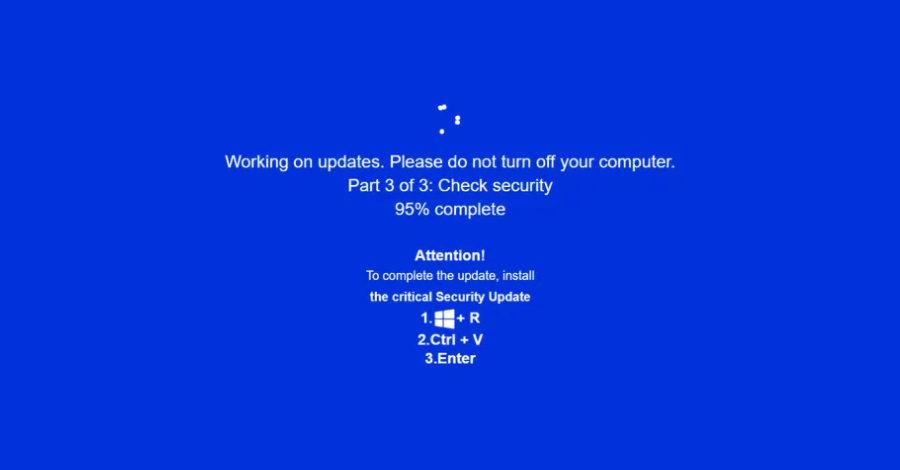
Cybersecurity researchers are calling attention to a new campaign that’s leveraging a combination of ClickFix lures and fake adult websites to deceive users into running malicious commands under the guise of a “critical” Windows security update. “Campaign leverages fake adult websites (xHamster, PornHub clones) as its phishing mechanism, likely distributed via malvertising,” Acronis said in […]
Black Friday 2025 is almost here, and early deals are already live across security software, online courses, system administration tools, antivirus products, and VPN services. These discounts are limited-time offers and vary by provider, so if you see something that fits your needs, it’s best to act while it’s available. […] Read More
Researchers built an inexpensive device that circumvents chipmakers’ confidential computing protections and reveals weaknesses in scalable memory encryption. Read More
Year-end budgeting is the perfect time to close real security gaps by strengthening identity controls, reducing redundant tools, and investing in outcome-driven engagements. The article highlights how targeting credential risks and documenting results helps teams maximize spend and justify next year’s budget. […] Read More
Thousands of credentials, authentication keys, and configuration data impacting organizations in sensitive sectors have been sitting in publicly accessible JSON snippets submitted to the JSONFormatter and CodeBeautify online tools that format and structure code. […] Read More
A new ClickFix variant ratchets up the psychological pressure to 100 and addresses some technical mitigations to classic ClickFix attacks. Read More