The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned network defenders of Chinese hackers backdooring VMware vSphere servers with Brickstorm malware. […] Read More
Microsoft is investigating and working to resolve a known issue that prevents customers from downloading Microsoft 365 desktop apps from the Microsoft 365 homepage. […] Read More
A maximum severity vulnerability, dubbed ‘React2Shell’, in the React Server Components (RSC) ‘Flight’ protocol allows remote code execution without authentication in React and Next.js applications. […] Read More
OT environments rely on aging systems, shared accounts, and remote access, making weak or reused passwords a major attack vector. Specops Software explains how stronger password policies and continuous checks for compromised credentials help secure critical OT infrastructure. […] Read More
Threat actors have been exploiting a command injection vulnerability in Array AG Series VPN devices to plant webshells and create rogue users. […] Read More
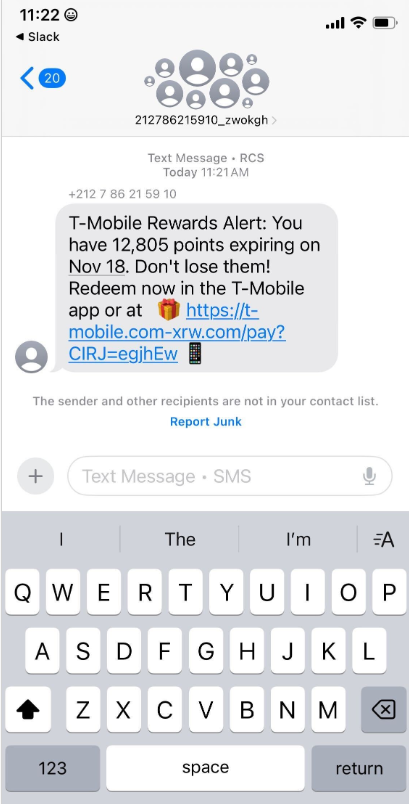
China-based phishing groups blamed for non-stop scam SMS messages about a supposed wayward package or unpaid toll fee are promoting a new offering, just in time for the holiday shopping season: Phishing kits for mass-creating fake but convincing e-commerce websites that convert customer payment card data into mobile wallets from Apple and Google. Experts say […]
U.S. prosecutors have charged two Virginia brothers arrested on Wednesday with allegedly conspiring to steal sensitive information and destroy government databases after being fired from their jobs as federal contractors. […] Read More
The threat actor known as Silver Fox has been spotted orchestrating a false flag operation to mimic a Russian threat group in attacks targeting organizations in China. The search engine optimization (SEO) poisoning campaign leverages Microsoft Teams lures to trick unsuspecting users into downloading a malicious setup file that leads to the deployment of ValleyRAT […]
Russian telecommunications watchdog Roskomnadzor has blocked access to Apple’s FaceTime video conferencing platform and the Snapchat instant messaging service, claiming they’re being used to coordinate terrorist attacks. […] Read More
CISA released nine Industrial Control Systems (ICS) Advisories. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-25-338-01 Mitsubishi Electric GX Works2 ICSA-25-338-02 MAXHUB Pivot ICSA-25-338-03 Johnson Controls OpenBlue Mobile Web Application for OpenBlue Workplace ICSA-25-338-04 Johnson Controls iSTAR ICSA-25-338-05 Sunbird DCIM dcTrack and Power IQ ICSA-25-338-06 SolisCloud Monitoring Platform […]