Table of Contents
What is Identity and Access Management?
Identity and Access Management (IAM) sits at the heart of modern cybersecurity strategies and business operations. But what exactly is IAM, and why is it so vital? At its core, IAM is the framework of policies, technologies, and processes that ensure the right people (or systems) have access to the right resources at the right time.
With data becoming an organization’s most valuable asset and rapidly rising cyber threats, IAM plays a pivotal role in safeguarding sensitive information, supporting regulatory compliance, and enabling smoother workflows. Whether you’re an IT professional, a business leader, or someone starting their cybersecurity learning path, this comprehensive guide will break down why IAM matters and how it forms the backbone of modern business security.
Let’s check out how IAM optimizes security, drives compliance, and scales with the needs of today’s digital enterprises.
Understanding Identity and Access Management Fundamentals
To fully grasp IAM’s value, understanding its key components and mechanisms is essential.
What is Identity and Access Management?
Identity and Access Management (IAM) is a strategic framework that ensures the appropriate level of access to resources within an organization. It addresses two essential questions:
- Who has access to specific resources?
- What can they do with that access?
IAM encompasses everything from authenticating a user’s identity to assigning permissions based on defined roles. Various organizations provide guidance and standards to refine and secure IAM practices:
- NIST (National Institute of Standards and Technology): NIST defines IAM as a critical component of cybersecurity, emphasizing authentication, federations, credential management, and access control policies. Frameworks like NIST SP 800-63 and 800-53 outline digital identity standards and security controls to mitigate risks.
- MITRE: MITRE focuses on IAM through its ATT&CK framework, identifying tactics and techniques related to adversary behavior, such as privilege escalation, credential dumping, and account manipulation. It highlights the importance of robust IAM systems to defend against these threats.
- CIS (Center for Internet Security): CIS emphasizes IAM in its Critical Security Controls (CSC), particularly in Control 6 (Access Control Management). It advocates for processes like least privilege, account monitoring, and multi-factor authentication to secure access to organizational resources.
- OWASP (Open Web Application Security Project): OWASP addresses IAM primarily in web application security. It highlights risks such as broken access control, improper authentication, and session management vulnerabilities in its OWASP Top Ten, underscoring the role IAM plays in safeguarding applications.
IAM is a foundational element of cybersecurity, with each organization contributing unique perspectives and standards to strengthen access management across various environments.
Understanding Identity vs Access Management
Though often grouped together, identity management and access management are distinct yet interconnected areas within the broader field of Identity and Access Management (IAM). Frameworks like NIST (National Institute of Standards and Technology) provide detailed definitions that highlight their roles in securing digital ecosystems:
- Identity Management: According to NIST, identity management involves creating, managing, and maintaining digital identities for users, devices, or services. This includes processes like identity proofing, credential issuance, updating user information, and ensuring identities remain accurate and secure throughout their lifecycle. Identity management forms the foundation for controlling access to systems and resources by ensuring that only verified entities are recognized within a system. For example, NIST Special Publication 800-63 outlines best practices for identity proofing and authentication management to ensure robust identity security.
- Access Management: NIST defines access management as the process of granting or restricting permissions to ensure users, devices, or services can perform only authorized actions. This involves implementing access controls, evaluating policies, and enforcing least privilege principles. Access management also includes continuous monitoring of access activities, ensuring policies are followed, and adapting permissions dynamically based on behavior or risk signals. For example, NIST SP 800-53 provides a catalog of controls to manage and enforce access effectively across systems.
Together, identity and access management work in tandem to ensure secure and efficient management of digital identities and their interactions with systems. By maintaining strong identity proofing and implementing strict access controls, organizations can align with established frameworks like NIST to enhance their overall security posture.
Core Elements of IAM
A successful Identity and Access Management (IAM) framework is built on several core components that ensure security, efficiency, and compliance within an organization:
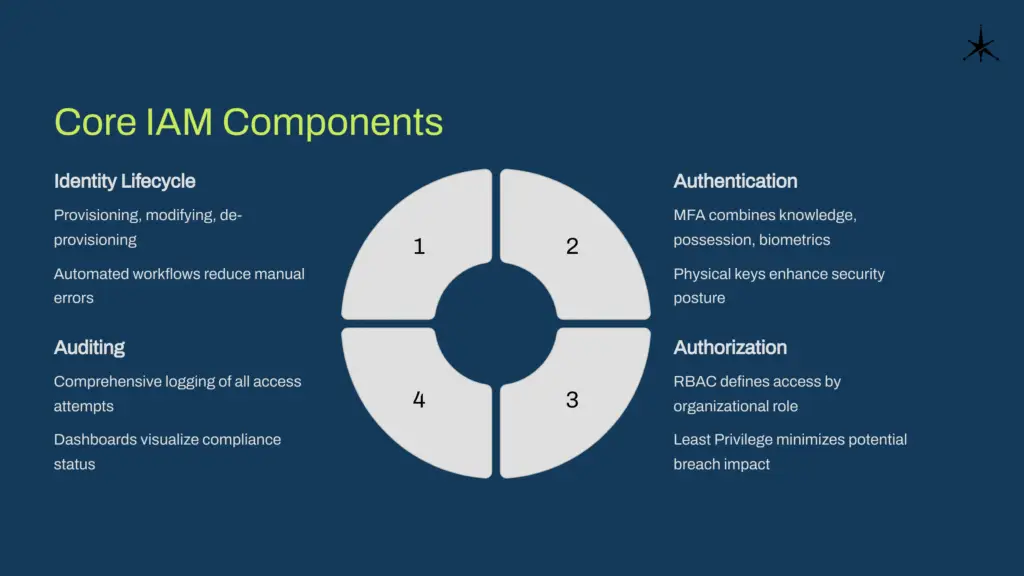
- Identity Lifecycle Management
This involves managing user identities throughout their entire lifecycle within an organization. It includes creating user accounts (provisioning) during onboarding, updating permissions as roles change (modifying access), and revoking access when users leave the organization (de-provisioning). Automation plays a critical role here by reducing manual errors, speeding up processes, and ensuring access changes are implemented promptly. Effective lifecycle management not only minimizes risks but also enhances operational efficiency.
- Authentication Mechanisms
Authentication is the process of verifying a user’s identity before granting access to systems or resources. Traditional passwords have been supplemented—or replaced—by more robust methods such as Multi-Factor Authentication (MFA), which requires a combination of factors like something the user knows (password), something they have (hardware token), and something they are (biometric data like fingerprints or facial recognition). Additionally, advancements in biometric access, including iris scans and behavioral biometrics, and the use of physical security keys or hardware tokens, have further strengthened authentication mechanisms. These methods ensure only legitimate users can access sensitive resources.
- Authorization Processes
Authorization determines what resources users can access and what actions they can perform once authenticated. This is governed by principles like Role-Based Access Control (RBAC), where access is granted based on a user’s role within the organization, and the Principle of Least Privilege (PoLP), which ensures users have only the minimum level of access necessary to perform their job. These principles reduce the risk of unauthorized access and limit the potential damage in case of a security breach. Granular access controls and policy enforcement are key to maintaining a secure and efficient system.
- Auditing and Reporting
Auditing and reporting are essential for maintaining transparency, ensuring security, and meeting regulatory compliance. Comprehensive tracking systems log every access attempt, change in permissions, and user activity across the network. These audit trails provide crucial evidence for regulatory compliance, internal investigations, and identifying potential security incidents. Regular reviews of audit logs help organizations detect anomalies, enforce accountability, and refine their IAM policies. Reporting tools often include visual dashboards and detailed summaries to make analysis more accessible for IT teams and decision-makers.
By integrating these elements, organizations can build a robust IAM framework that safeguards sensitive information, supports compliance efforts, and enhances overall operational efficiency.
The Business Case for IAM
Identity and Access Management (IAM) isn’t just a tool for enhancing security; it’s a strategic business enabler that drives efficiency, cost savings, and smooth user experiences. Here’s a closer look at how IAM impacts the operational and financial aspects of enterprises.
Cost Benefits of Security Breach Prevention
Data breaches are becoming increasingly common and costly. The average cost of a data breach globally is $4.88 million, according to IBM’s 2024 Cost of a Data Breach Report. Beyond the direct financial loss, breaches also come with reputational damage, regulatory fines, and operational disruptions. An effective IAM program reduces these risks by ensuring only authorized users have access to critical systems and sensitive data. By proactively mitigating threats, organizations of all sizes can avoid these hidden costs, making IAM a smart long-term investment.
High-Profile Breaches and Vulnerabilities: Lessons in IAM Challenges
Social engineering played a key role in this attack, where threat actors successfully manipulated the Okta service desk into resetting passwords and MFA configurations. By gaining privileged access, the attackers crippled vital hotel operations for multiple days. This breach underscores the critical importance of rigorous identity verification processes and the need for robust service desk protocols.
Caesars Entertainment (Sep 2023)
Similar to the MGM Resorts attack, outsourced IT support became the entry point for attackers. By compromising Okta MFA resets, they exfiltrated sensitive loyalty program data. Reports suggest a ransom was paid, highlighting the financial and reputational dangers of supply-chain vulnerabilities.
Okta Support System (Sep–Oct 2023)
A service-account token left exposed in a personal browser session became a weak link, allowing intruders to extract HAR files containing active admin cookies. This incident affected 134 customers, emphasizing the risks of privilege misuse and the consequences of improper session management.
Microsoft Storm-0558 (Jul 2023)
Sophisticated attackers exploited the theft of a consumer signing key, enabling them to forge OAuth tokens that bypassed Azure AD authentication. The breach resulted in unauthorized access to government mailboxes, showcasing the vulnerabilities tied to credential management.
By phishing users of a support tool, attackers captured administrative credentials and exported 133 customer mailing lists. This incident highlights the dangers of weak phishing defenses and insufficient access control.
A malware attack on an engineer’s laptop compromised a 2FA-backed SSO session cookie, enabling the attacker to mint production tokens and steal customer secrets. This breach demonstrates the critical need for endpoint security and monitoring.
A keylogger installed on a DevOps engineer’s home PC allowed attackers to capture corporate vault credentials and S3 keys. This led to the theft of encrypted customer vaults, emphasizing the importance of securing remote work environments and using hardware-based authentication.
The Yanluowang group exploited credentials from an employee’s personal cloud drive and used “MFA fatigue” attacks; sending repeated push notifications to trick users into accepting a request. This method enabled VPN access and internal data theft, showing how fatigue tactics can undermine MFA protections.
Attackers purchased VPN credentials from a contractor and used relentless push-MFA spam to gain full admin access. The breach was exposed via a public Slack post, highlighting the gaps in credential hygiene and secure authentication practices.
DarkSide ransomware operators exploited a dormant VPN account without MFA, causing a five-day shutdown of a critical fuel pipeline. This incident revealed how even unused accounts lacking proper security measures pose significant risks.
Each of these high-profile breaches underscores the need for a comprehensive identity and access management (IAM) strategy. By addressing weak points such as credential misuse, session vulnerabilities, and social engineering risks, organizations can better protect both their infrastructure and reputation. Effective IAM practices, combined with ongoing employee training and technology investment, are key to mitigating the evolving threat landscape.
Streamlining Workflows and Enhancing Efficiency
IAM solutions go beyond access control, they also optimize workflows. Automated provisioning and deprovisioning save IT teams countless hours by removing the need for manual account management, while single sign-on (SSO) capabilities simplify access to multiple tools and platforms. Employees also benefit from quicker, hassle-free access to the tools they need, reducing downtime and support requests. This efficiency not only boosts employee productivity but allows IT teams to focus on higher-value projects instead of repetitive tasks.
Failing to promptly disable user accounts of former employees poses a significant security risk and can result in compliance violations. When accounts remain active after an employee’s departure, they create a potential entry point for unauthorized access. Whether intentionally exploited by a disgruntled former employee or accidentally accessed by another party, these accounts can be used to access sensitive company data, manipulate internal systems, or disrupt operations. From a compliance perspective, regulations like GDPR, HIPAA, and others mandate strict controls over access management, and leaving active accounts unaddressed could lead to non-compliance, resulting in fines or legal consequences. Addressing this proactively through identity and access management policies, including automated deprovisioning tools, is vital to maintaining organizational security and regulatory adherence.
Improving User Experience
IAM doesn’t just secure resources; it enhances usability. Simplified login processes, such as SSO or passwordless authentication, reduce the frustration of juggling multiple credentials. This means employees, customers, and partners can focus on their work or engagement without unnecessary disruptions. A smoother user experience also contributes to higher satisfaction and loyalty, particularly in customer-facing applications where ease of use can make or break the user journey.
Enabling Digital Transformation
Robust IAM solutions empower companies to embrace digital transformation with confidence. By safeguarding access to cloud platforms, applications, and data, IAM allows businesses to adopt modern technologies without fear of compromising security. This is particularly critical for organizations supporting remote or hybrid work environments, where seamless yet secure access is essential. Additionally, IAM facilitates secure collaboration with external partners and vendors, breaking down barriers to innovation and growth while maintaining control over sensitive information.
IAM is a foundational element that supports growth, innovation, and operational excellence in today’s digital-first world. Businesses that invest in a comprehensive IAM strategy gain not only stronger security but also the flexibility to adapt to evolving demands and opportunities.
IAM as the Foundation of Information Security
IAM is often referred to as the “new security perimeter,” a term that highlights its criticality in today’s landscape of remote work and distributed networks.
The Principle of Least Privilege and Zero Trust
IAM (Identity and Access Management) ensures users only have the minimum permissions needed to perform their roles, a key practice rooted in the Principle of Least Privilege. This principle minimizes the risk of unauthorized access by restricting users to only what is absolutely necessary for their tasks (NIST Special Publication 800-207).
At the heart of modern cybersecurity, IAM closely aligns with Zero Trust Architecture (ZTA), a security philosophy and framework built on the assumption that no user, device, or asset should be implicitly trusted—whether inside or outside the network. Instead of relying on perimeter-based defenses, ZTA adopts a “never trust, always verify” approach ([NIST SP 800-207, Section 2](https://doi.org/10.6028/NIST.SP.800-207)), requiring continuous validation of identity, access, and activity across all resources.
Zero Trust operates on three core principles (NIST SP 800-207, Section 3.1):
- Verify explicitly – Continuously authenticate and authorize users and devices based on all available data points, such as user identity, location, and device posture.
- Use least privilege access – Limit access to only what is necessary, reducing potential damage from compromised accounts or insider threats.
- Assume breach – Design systems with the assumption that breaches can and will happen, focusing on real-time monitoring, rapid detection, and containment of threats.
By combining IAM with Zero Trust principles, as outlined in the NIST Zero Trust Architecture framework (NIST SP 800-207), organizations can create a robust system to secure sensitive resources, mitigate risks, and proactively defend against evolving cyber threats. Together, these principles establish a dynamic and adaptive security model, ensuring that access is tightly controlled and continuously evaluated.
Defense in Depth
IAM contributes significantly to a defense-in-depth strategy. By layering strong user authentication, precise access controls, and continuous monitoring, IAM helps thwart multi-vector attacks.
IAM’s Role in Modern Cybersecurity
IAM connects with other domains, including API management, data encryption, and endpoint protection. It acts as the glue that ties these systems together while ensuring that identity remains central to security.
Ensuring Regulatory Compliance
The IAM Compliance Mandate
IAM (Identity and Access Management) plays a crucial role in helping organizations meet the requirements of major regulations, ensuring secure and compliant operations. Here’s how IAM aligns with specific mandates:
- GDPR (General Data Protection Regulation):
- Requires secure authentication mechanisms to ensure only authorized users access personal data.
- Enforces the principle of “data minimization,” meaning users should only access data necessary for their role.
- Demands audit trails to track who accessed personal information and when, aiding in accountability and breach response.
- HIPAA (Health Insurance Portability and Accountability Act):
- Requires implementation of role-based access controls to restrict access to electronic protected health information (ePHI) only to necessary personnel.
- Mandates user authentication systems to verify identities before granting access to sensitive data.
- Specifies the need for audit controls to log and monitor access to ePHI for detecting and preventing misuse.
- SOX (Sarbanes-Oxley Act):
- Mandates monitoring and control over user access to financial systems to prevent unauthorized changes to financial records.
- Requires periodic access reviews to ensure that only appropriate personnel have system or data access.
- Enforces segregation of duties to minimize conflicts of interest, ensuring that no single individual has control over all parts of a financial transaction.
- PCI DSS (Payment Card Industry Data Security Standard):
- Requires strong access controls, including multi-factor authentication, to limit who can access cardholder data.
- Enforces the principle of least privilege, ensuring users only have access to data necessary for their role.
- Demands regular access reviews and logging of all actions performed on systems handling cardholder data to identify and investigate anomalies quickly.
By addressing these specific requirements, IAM solutions enable organizations to maintain compliance while enhancing security, reducing risk, and building customer trust.
Audit Trails and Reports for Compliance
IAM’s logging and reporting capabilities are invaluable for maintaining detailed audit trails, which are often mandated during compliance audits. These features ensure that every user action is recorded, providing a clear, traceable history of access and changes within the system. With comprehensive reports, organizations can demonstrate adherence to regulatory requirements, identify potential security risks, and address them proactively, making IAM a crucial tool for achieving and maintaining compliance.
Tackling IAM Challenges While Scaling
Managing Hybrid and Cloud Environments
As organizations scale, one of the biggest challenges in Identity and Access Management (IAM) is managing access across both cloud platforms and traditional on-premise systems. The increasing adoption of hybrid environments brings complexity, as businesses need to ensure consistent policies and visibility across varied infrastructures. Hybrid IAM solutions are designed to address this challenge by bridging the gap between cloud and on-premise systems, offering unified visibility and centralized control. This ensures secure and seamless access for users, no matter where the resources are hosted.
Securing Privileged Accounts
Privileged accounts, such as administrator or root accounts, are highly attractive targets for cybercriminals because they provide access to critical systems and sensitive data. Mismanagement of these accounts can lead to catastrophic breaches. Implementing Privileged Access Management (PAM) solutions adds an extra layer of security by introducing features such as session recording, which monitors and logs all actions in real time, and just-in-time access, which grants access only for specific tasks and for a limited duration. These safeguards help organizations minimize risk and maintain tight control over their most sensitive accounts.
Balancing Security and User Experience
IAM solutions must find the right balance between enforcing strong security measures and providing a frictionless user experience. Overly strict security protocols can frustrate users and hinder productivity, while too much leniency can leave systems vulnerable. Adaptive authentication powered by AI is a game-changer in this area. It analyzes user behavior, location, device, and context to dynamically adjust access requirements. For instance, a user logging in from their usual location on a familiar device might face minimal barriers, while an attempt from an unusual location triggers additional verification steps. This approach enhances security while maintaining a smooth user experience.
Addressing Shadow IT
Shadow IT, or the use of unauthorized tools and applications by employees, poses a major risk to organizational security. These tools often bypass official IT oversight, increasing the chances of data breaches and compliance issues. IAM tools equipped with monitoring capabilities can detect and secure unsanctioned apps, providing IT teams with the visibility they need to manage risks effectively. By implementing policies that encourage safe and approved tool adoption, organizations can mitigate the risks associated with shadow IT while fostering innovation and productivity.
Artificial Intelligence and the Future of IAM
AI is revolutionizing Identity and Access Management (IAM) by enhancing security, efficiency, and adaptability.
- Leveraging IAM Mechanisms: AI integrates with IAM systems to analyze user behavior, detect anomalies, and respond to potential threats in real-time. Features like behavioral analytics and adaptive authentication enable dynamic risk-based access decisions, ensuring security without hindering the user experience. Additionally, automated access reviews simplify the identification of unused or excessive permissions, reducing the risk of insider threats.
- IAM Governing AI: As AI becomes more integral to business operations, IAM plays a pivotal role in governing AI workloads and AI agents. IAM ensures secure access to AI models, data, and tools by managing permissions and enforcing role-based policies. By tightly controlling who or what has access to AI systems, IAM mitigates the risks of unauthorized AI usage, data breaches, or adversarial attacks. This governance ensures AI is used responsibly while safeguarding sensitive workloads.
- Protecting AI Workloads: IAM helps organizations secure and optimize AI workloads by providing robust authentication and authorization mechanisms. It protects AI agents—both human and machine—by regulating their access to critical resources and ensuring that usage aligns with organizational policies. This layered protection helps maintain the integrity and confidentiality of AI systems, preventing misuse or exploitation.
- Treating AI in IAM: While AI improves IAM processes, it must be handled with care. Transparency is critical—organizations must ensure that AI models are explainable and auditable to maintain trust. AI must be continually monitored, trained on diverse datasets, and aligned with ethical guidelines to avoid biases or errors that could compromise security or fairness.
By balancing AI’s capabilities with responsible practices and leveraging IAM to govern and protect AI systems, organizations can maximize the potential of IAM while ensuring security, efficiency, and ethical integrity.
Managing Machine and API Identities
With the rise of AI systems and APIs, managing unique digital identities has become increasingly critical to ensure security and accountability. These identities help verify and authorize interactions between machines, APIs, and users, preventing unauthorized access or misuse. Technologies like OAuth, which provides secure delegated access, and certificate-based mechanisms, which enable encrypted communication and authentication, are at the forefront of this effort. By implementing these tools, organizations can create a trusted digital ecosystem where machine-to-machine and API communications are both efficient and secure.
Starting Your IAM Journey
Implementing Identity and Access Management (IAM) within your organization can feel like a daunting task, but with the right approach, it becomes manageable and highly effective. A strong IAM strategy not only enhances security but also streamlines access for users, driving productivity. Here’s how to simplify and optimize the process.
Assess Current IAM Maturity
Begin by evaluating your existing IAM infrastructure. Identify areas of weakness, including outdated technologies, manual processes, or inconsistent access controls. Determine vulnerabilities, the risks they pose to your organization, and prioritize what requires immediate attention versus longer-term improvements. This assessment will give you a clear picture of where your organization stands and what needs to be addressed.
Develop an IAM Roadmap
Create a phased strategy that aligns your IAM efforts with your business objectives. Start with quick wins, such as enabling Multi-Factor Authentication (MFA) across critical systems to immediately improve security posture. Then map out long-term goals, like building a zero-trust framework that ensures every access request is verified, regardless of location or device. Clearly define milestones to track your progress and coordinate IAM initiatives with other IT and cybersecurity goals.
Select the Right IAM Solution
Choosing the right IAM platform is critical to the success of your implementation. Consider factors like the size of your organization, the complexity of your IT environment, and your industry’s specific regulatory requirements. Look for solutions that offer flexibility, scalability, and compatibility with your existing tools and systems. Features like automated user provisioning, role-based access control, and analytics should also be evaluated to ensure the solution meets both current and future needs.
Follow Best Practices for Adoption
A successful IAM implementation requires more than just technology, it depends on people and processes too. Keep these best practices in mind:
- Gain executive buy-in early: Ensure leadership understands the importance of IAM and provides the necessary support and funding.
- Provide training for employees: Educate users about the importance of secure access practices and how IAM impacts their daily workflows.
- Create clear IAM policies: Establish consistent, enforceable policies around user access, password management, and system monitoring.
- Regularly measure IAM performance: Use key metrics, such as the number of unauthorized access attempts prevented or time saved on user provisioning, to gauge the effectiveness of your IAM system.
By following these steps and committing to continuous improvement, you can build a strong, scalable IAM foundation that enhances both security and efficiency across your organization.
Identity and Access Management Is Business Security
In today’s digital landscape, Identity and Access Management (IAM) is no longer an option; it’s a necessity for organizations of all sizes. With cyber threats on the rise, comprehensive IAM frameworks are essential for protecting sensitive data, ensuring only the right people access the right resources at the right time. IAM helps you align with global compliance standards, build customer trust, and improve operational efficiency by enabling seamless, secure access to your systems and applications.
Don’t wait for a security incident to emphasize how critical IAM is to your business. Proactively safeguarding your organization with a robust IAM strategy not only reduces risk but also sets the foundation for scalable growth in an increasingly interconnected world. Begin your IAM transformation today to stay ahead of emerging threats and maintain complete control over access to your digital ecosystem.